Azure Arc is a new service from Microsoft that enables you to manage and monitor your on-premises and hybrid servers using the same tools and processes as you use for managing Azure resources. With Azure Arc, you can deploy and manage your servers using Azure Resource Manager templates, apply policies and compliance standards to your servers, and monitor and troubleshoot your servers using Azure Monitor and Azure Log Analytics.
Azure Arc is gaining popularity among organizations that want to manage their on-premises and hybrid servers in a consistent and centralized manner and benefit from the advanced features and capabilities of Azure. One of the key features of Azure Arc is the ability to use Azure VM extensions on your own infrastructure, which allows you to extend the functionality of your servers and automate common tasks.
Revolutionize Your Security Operations with Microsoft Sentinel
In my recent blog posts, I have described how to use Azure Arc to install the Custom Script Extension for Windows on your Arc-connected nodes. The Custom Script Extension allows you to run PowerShell or Bash scripts on your Azure VMs and can be used to automate various tasks, such as installing software, configuring settings, and applying updates.
In my blog posts, I provide step-by-step instructions for using the Custom Script Extension with Azure Arc. I recommend reading both of these posts:
- Azure Arc Custom Script Extension for Windows
- Azure Arc for Servers Extensions – Making it easier to manage your servers
Allowing to execute PowerShell scripts from different places comes with higher risks, and that bad guy can do the same. Many companies are already using Microsoft Sentinel for their SIEM and SOAR. If you are not doing that today, I strongly recommend testing it out.
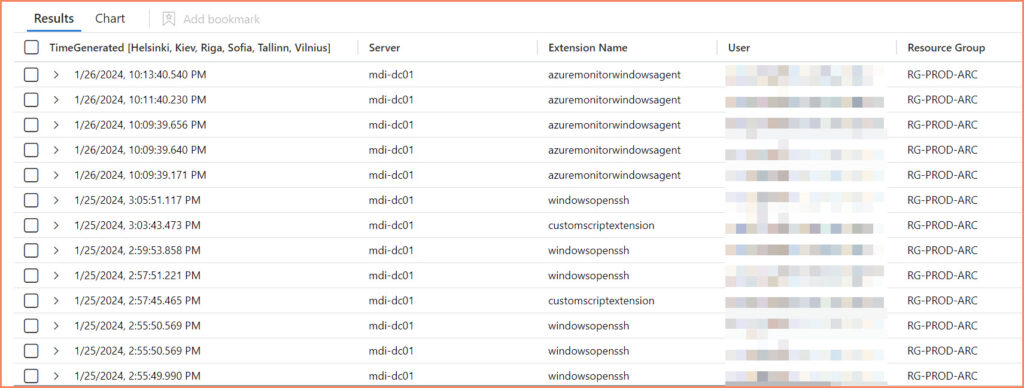
To get visibility from your environment around extension installation etc., I put together the following KQL query. You can use this for Workbooks or for detections.
AzureActivity | where OperationNameValue == "MICROSOFT.HYBRIDCOMPUTE/MACHINES/EXTENSIONS/WRITE" and ResourceProviderValue == "MICROSOFT.HYBRIDCOMPUTE"
| extend Properties = (parse_json(Properties))
| extend Server = split(Properties.resource,"/")[0]
| extend ["Extension Name"] = split(Properties.resource,"/")[1]
| extend User = Properties.caller
| extend ["Resource Group"] = Properties.resourceGroup
| extend ["Susbcription ID"] = Properties.SubscriptionId
| extend ["IP Address"] = CallerIpAddress
| extend ["Activity Status"] = Properties.activityStatusValue
| project TimeGenerated,Server, ['Extension Name'], User, ['Resource Group'], ['Susbcription ID'], ['IP Address'],["Activity Status"]
| sort by TimeGenerated