As an Entra ID administrator, reviewing privileged accounts is crucial to ensure they are used appropriately and regularly. One essential aspect of these audits is to monitor the last sign-in activity data for privileged accounts. By doing so, you can identify accounts that are no longer in use and revoke their access, thereby minimizing the risk of security breaches. In this post, we’ll guide you through the process of querying Entra ID last sign-in activity data using PowerShell and show you how to use the data for auditing privileged accounts.
You can create various scripts for auditing purposes, such as guest users, synchronized identities from on-premises Active Directory, and more. Using these scripts, you can identify active or inactive accounts based on the results.
Prerequisites
- Entra ID Global Administrator
- Latest Microsoft Graph PowerShell module
- PowerShell 7.x
- Visual Studio Code
Step 1: Install Microsoft.Graph PowerShell Module
First we need to install the Microsoft Graph PowerShell module:
Install-Module -Name Microsoft.Graph -Force -Verbose
Step 2: Define the desired permission scopes
We need to define the permission scopes required to access role management information in Entra ID. The following scopes are required to retrieve information about eligible role assignments:
$Scopes = @(
"User.Read.All",
"Directory.Read.All",
"AuditLog.Read.All"
)
If you are unsure how to define the permissions scope for a particular command, you can try using the Find-MgGraphCommand cmdlet. While this command may not provide all the information you need, it can still give you some helpful hints.
Step 3: Connect to Microsoft Graph API
To connect to the Microsoft Graph API run the following command:
Connect-MgGraph -Scopes $Scopes
Step 4: Get the Entra ID User Last Sign-In Data
To retrieve the last sign-in activity data for a specific user, use the Get-MgUser cmdlet with the -UserId parameter to specify the user’s object ID and the -Property parameter to retrieve the sign-in activity data. For example:
$UserData = Get-MgUser -UserId XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX -Property "SignInActivity"
$UserData.SignInActivity
This command retrieves the sign-in activity data for the specified user. Note that the -Property parameter is required to retrieve the sign-in activity data. If you do not include the -Property parameter, the SignInActivity attribute will be empty.
If you want to retrieve the last sign-in activity data for a handful of users, use the Get-MgUser cmdlet with the -Filter parameter.
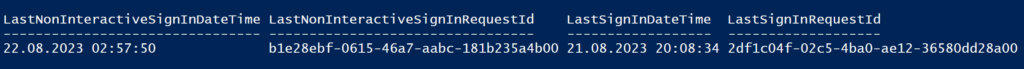
You should see the following output from the test user:
- LastNonInteractiveSignInDateTime
- LastNonInteractiveSignInRequestId
- LastSignInDateTime
- LastSignInRequestId
Step 5: Export Entra ID User Last Sign-In Data to a CSV File
Now that we have retrieved the last sign-in activity data, we can export it to a CSV file. To do this, use the Export-Csv cmdlet and specify the output path as shown below:
$UserData = Get-MgUser -UserId XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX -Property "SignInActivity"
$UserData.SignInActivity |
Select-Object -Property LastNonInteractiveSignInDateTime,LastNonInteractiveSignInRequestId,LastSignInDateTime,LastSignInRequestId |
Export-Csv -Path C:\temp\USERDATA.CSV
This command exports certain property values to a CSV file named USERDATA.CSV
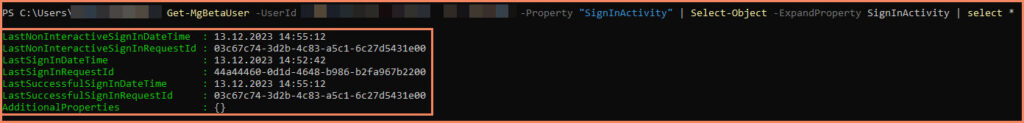
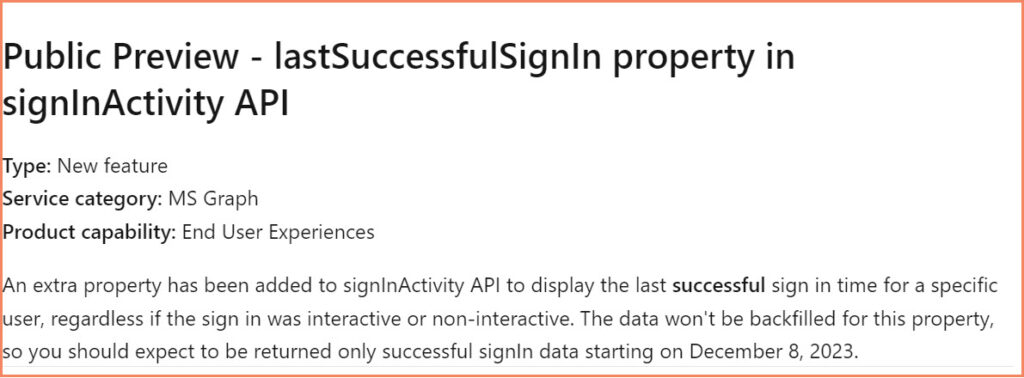
NEW! – LastSuccessfulSignIn property
Microsoft added a new property to the Beta API called LastSuccessfulSignIn. You need to use the Beta cmdlets to read that information.
Conclusion
Auditing privileged accounts is critical to maintaining a secure Entra ID environment. Monitoring last sign-in activity data helps identify accounts no longer in use and reduces the risk of security breaches. With the help of PowerShell and the Microsoft Graph PowerShell module, administrators can easily retrieve the last sign-in activity data for users and implement auditing scripts for different purposes. By regularly reviewing and updating privileged accounts, organizations can ensure that access to sensitive resources is granted only when necessary, minimizing the risk of security incidents.